2 Malware and Viruses
Risks
The terms “malware” and “virus” are often used interchangeably; however, there is a subtle distinction. Malware is a generic term for any type of malicious software, whereas a virus is a specific type of malware that replicates and can be passed from computer to computer (analogous to how a flu virus would be transmitted from person to person). When microcomputers were first introduced, it was primarily viruses that were the cause of concern, so people installed “anti-virus” software. The threats today come from a broader spectrum referred to as malware, but it is not uncommon to hear people use the word “virus” when more correctly what they are referring to is “malware.”

When software is written for computing devices (computers, tablets, phones, etc.), programmers need to be able to write “perfect” code so that no malicious use of the software occurs (be it program, app or operating system). Even with testing for quality assurance, software only approaches “near perfect”, leaving room for a programmer with malicious intent to exploit some unintended opening. The malicious software is referred to as “malware”.
Types of malware cover a broad spectrum:
- Adware: Aggressive advertising that appears on your computer screen constantly.
- Spyware: Gathers your personal information (without your knowledge) with the intent of identity theft, impersonation or fraud.
- Scareware: Typical scareware would be a message such as “Danger, your computer is infected, click here to fix the problem” when in fact your computer is not infected, and by clicking on the link to supposedly fix your computer, you actually end up downloading and installing malware on your computer instead.
- Ransomware: The encrypting of your data (files, pictures, music, etc.) so you can’t access it anymore unless you pay a ransom to un-encrypt it. Ransomware has been used to target individuals (with ransoms of a few hundred dollars), as well as large corporate entities (with ransoms in the millions of dollars). In 2021, Colonial Pipeline (which delivers 100 million gallons of fuel a day) temporarily closed its operations when ransomware was found on its computer systems. The shutdown affected the supply of gasoline in large parts of the US East Coast. The company made a ransom payment to hackers in excess of $4 million in order to restore pipeline operations. In an interesting twist, the FBI hacked the hackers “digital wallet” and recovered a large portion of the ransom.
- Virus: Designed to damage the operation of your device by deleting, corrupting or slowing your device’s operation. Viruses require a computer user to do something to help them spread (e.g. download and run a file, run a macro, etc).
- Worm: A type of malicious software similar to a virus, but with an important distinction, worms spread through computer networks without the assistance of a computer user.
- Trojan: Like the name implies, software that purports to do something useful, but also contains malware. For example, “See this Hollywood star caught in a compromising video, click here to download software to view the video”. If you click on the link, you will view a video, but end up installing some malicious software at the same time.
- Remote Control: Background control of your computer (without your knowledge) to perform malicious activity.
- Keyloggers: Software that records the keys you press, typically used to capture the addresses of web sites you visit, and your username and password. Be cautious of computers in public places (e.g. libraries, coffee shops, etc.) that might be infected, just browse the Internet, and don’t visit any websites that you would need to type in your username and password.
Malware Symptoms
With appropriate anti-malware software (also called antivirus) installed on your computer, and thinking critically about any messages you receive about installing software on your device, you should be able to avoid malware infections. If your computer exhibits any of the following symptoms, you may wish to perform a scan to check for malware on your system:
- Slower than usual computer or web browser speeds
- Programs freezing or crashing
- Excessive background activity
- Emails your friends receive, apparently from you, but you didn’t send
If you have anti-malware (antivirus) software installed on your device, you can run this program (app), and look for a choice that will allow it to “Scan.”
If you don’t have antivirus software installed, there are a number of websites you can go to that will perform a free scan of your device. Search for “free online antivirus”, and look at the search results (rather than the “Ads)”. TrendMicro and AVG are well known for their free online antivirus tools.
Malware Prevention
Thinking Critically
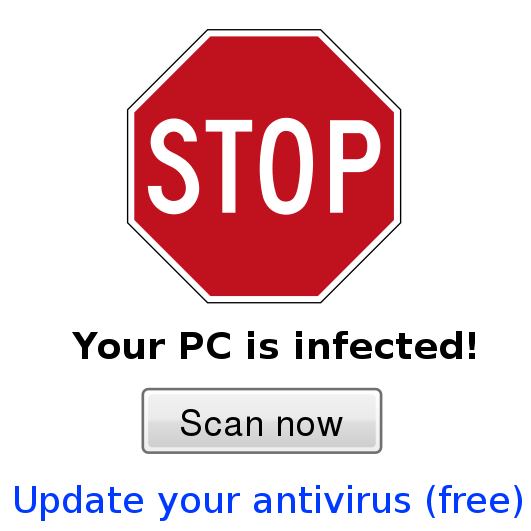
If your device displays a message urging you to take some action, think critically whether this message seems legitimate. For example:
You see a message claiming that your computer has a malware infection, and you need to do something to fix it. Did the message appear when you weren’t doing anything on your computer (so perhaps it’s a legitimate background process of your anti-malware program), or were you browsing the web and this message appeared (so perhaps it’s a malicious web site displaying a fake message trying to imitate a legitimate message from your anti-malware software).
If a website wants you to download and install software to view a video, you would ask yourself, Since I am able to view other videos on my device without downloading software, why would I need to do anything special to view this particular video? Is it really a different video format, or perhaps something malicious is in the download?
Anything that asks you to “download” or “make changes to your computer.” If this is coming at an unexpected time (i.e., you were doing something else on your device), exercise caution.
Another example is unsolicited phone calls claiming that your computer is infected and you need to follow the caller’s instructions on how to fix it. In actuality, your computer is fine, and if you follow the caller’s instructions, you will end up downloading and installing malware.
High Risk Activities
Certain activities can put your device at higher risk of contracting malware, or exposing personal information. Two of the largest risks come from:
Wi-Fi hotspots with no password. A Wi-Fi hotspot is a public location (e.g., a coffee shop or restaurant) where the business allows customers to connect wirelessly to the Internet. When connecting to a Wi-Fi hotspot that doesn’t have a password, communication between your device and the hotspot is “in clear,” i.e. what you type could be seen by someone else also connected to the hotspot (if they are using special software for this purpose). If you are using a Wi-Fi connection that doesn’t require you to type a password when you first join the hotspot, restrict your activity to browsing the web, and don’t enter any personally identifiable information or usernames and passwords. You can tell if your hotspot is broadcasting in clear (i.e. no encryption) by looking at the Wi-Fi setting on your device, and for hotspots with no passwords you should see an open padlock beside the hotspot name.
Browsing porn websites. Malicious programmers trying to infect computing devices want to infect as many devices as possible, and as porn is a common search on the web, creating an infected porn website has been one of the more common ways of distributing malware.
Anti-Malware (Antivirus) Software
Today, the terms anti-malware and antivirus are often used interchangeably and generally refer to the same thing; although anti-malware is a more technically correct description of the function of the software, the term antivirus is still widely used by many security software vendors as it is a more familiar term for many people.
Anti-malware (antivirus) software is designed to detect, prevent and remove malicious software from computing devices. You can conduct a web search for “anti-malware reviews” to see current recommendations for free and paid software for your device(s).
The current Windows operating system includes the Microsoft Defender program (previously called Windows Defender). The Mac operating system doesn’t currently have an Apple developed antivirus or anti-malware program. Virus and malware programmers have focused more on Windows PCs (simply because there are more of them than Mac computers), but it is a myth that Macs don’t get viruses/malware infections, there are just fewer malware programs written for Macs, so in that sense there is less chance of infection, but the chance does exist.
Which anti-malware/antivirus program you use is likely not as important as whether you have an anti-malware/antivirus program installed and running on your computer.
Your anti-malware/antivirus program typically is set up to automatically download a list of known malware to search for. As new malware is being created all the time, it’s important that your antivirus always has the latest list of malware to scan for.
It’s also important that you regularly scan your device for malware. Often, antivirus programs are set up to run in the early morning hours when the device is not being used.
Media Attributions
- “Malware” by EpicTop10.com is licensed under a CC BY 2.0 licence.
- “Malvertising” by Syced is made available under the CC0 1.0 Universal Public Domain Dedication.

